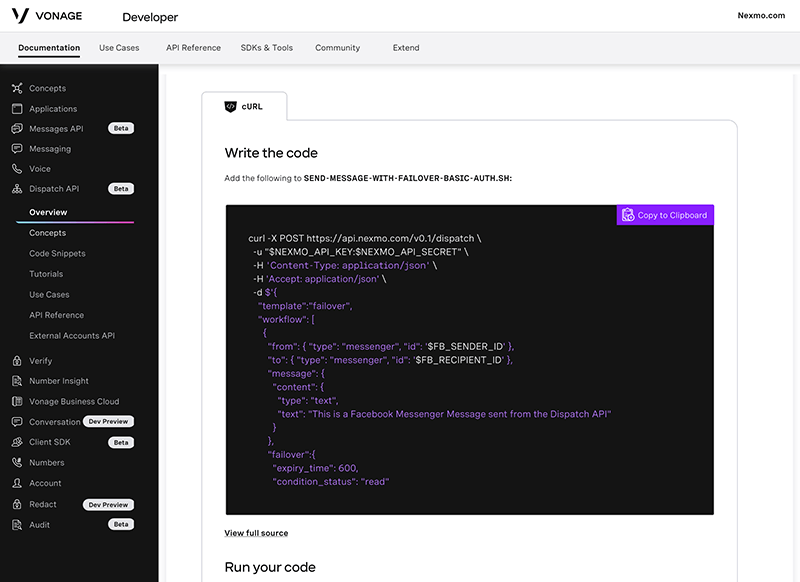
Security
Keep your data and business protected with security you can trust, from Vonage APIs.Redundancy, availability and uptime
We're committed to supplying a highly available platform and we do our best to minimise outages. Through the use of a content delivery network, geographically redundant data centres and redundancy within each data centre, we make sure failovers exist at several levels to maximise uptime. Information about availability and outages can be found on our status page. We also take regular offsite backups of important data to guarantee business continuity.Security testing
We support the responsible disclosure of vulnerabilities and believe it strengthens the security of our services. We also conduct periodic audits of application security and periodic third-party testing to discover and address any identified vulnerabilities.Physical security
Our servers are hosted by IBM Softlayer and AWS in data centres in Europe, the United States and SE Asia. Softlayer provides us with hardware, network connectivity and secure physical space relating to our customer data. Softlayer is compliant with ISO 27001 and other security standards.System security
We use firewalls and logical access control to protect our servers from unauthorised system access, allowing only trusted operations personnel to manage our systems. We also make sure to use strong configuration standards to harden our servers and we keep them up-to-date with the latest security patches.Application security
We support strong cryptography for communication over public networks, so that your Vonage API Dashboard password, API secret and the content of your communications may be protected in transit:- Between customers and Vonage APIs: HTTPS, SMPP-over-SSL, SIPS, SMPP, SIP, RTP
- Vonage API Dashboard: HTTPS
- Between Vonage APIs and carriers: HTTPS, SMPP-over-SSL, SIPS, SMPP-over-IPsec, HTTP, SMPP, ENUM, SIP, RTP
Encryption
We still support unencrypted protocols on the customer side in response to customer demand, but we strongly encourage customers to use secure protocols. Rest assured, the security of your data is unaffected by the communications protocols used by our other customers because of the logical segregation between customer accounts.
In connection with the provision of our services, we have secured direct relationships with telecommunications carriers and similar services providers around the globe. While many of our connections with these carriers are secure, some of these “last-mile” connections are unencrypted. This is beyond our control and depends on the carrier, as some telecommunications providers have legacy infrastructure and do not currently support secure protocols. We opt for secured communication with carriers when available.
Account management and access
We have rate limiting in place on API calls and Vonage API Dashboard logins to prevent brute force attacks. Password complexity requirements are enforced on API secret and Vonage API Dashboard password.
Vonage API Dashboard passwords are cryptographically hashed before storing in our database.
The Vonage API Dashboard supports two-factor authentication (2FA using our Verify API) when elected for customers who want to add an additional access control. If this is enabled, Vonage API Dashboard logins require an additional verification code, which is sent by SMS or automated phone call to the phone registered on your account, to be entered when logging in from an IP address which differs from the one used on the previous successful login.
On request, we can enable restrictions on a Vonage API Dashboard account such that it can only be logged into from specified IP addresses.
Accounts are logically segregated from each other and we use role-based access control within our company for access to systems and information.